SentinelOne - Automating the $HIT out of cybersecurity
SentinelOne is set up for success with a long runway, hypergrowth, excellent execution, high sales efficiency, and being founder-led with a never-ending mission to change cybersecurity.
Disclaimer: The information provided is not financial, investment, tax, or other advice. Nothing contained constitutes a solicitation, recommendation, endorsement, or offer to buy or sell securities or other financial instruments. For more information, read the disclaimer.
SentinelOne Founder Tomer has a great video pitching SentinelOne; check it out for a quick start.
What is SentinelOne’s Founding story?
To understand SentinelOne, I love to gain insights from the following founder letter.
SentinelOne was founded to solve the problem of cybersecurity in 2013. They didn’t hit the ground running and had to work really hard and innovate for 5 years to build an amazing product and platform. They didn't have any sales till the year 2018. They have pivoted over time to find the right strategy and get their foot into the door, with the industry’s first platform that is multi-tenant, fully autonomous, developer-friendly, and cloud-native. Check out the above founder’s letter; I love their commitment to their mission, pledge, and their driving principles. I love their focus on building trust and being a force for good in the world. Their principles of accountability and commitment to creating value are something that every investor seeks. Also, you can see they are an engineering-driven organization with principles of responsible marketing and relying on facts. These are also incredibly well aligned with great investors.
What is SentinelOne’s Mission?
SentinelOne has a simple mission to “Keep the world running”.
Their platform and technology are inspiring and combined with their mission they have tremendous optionality to secure everything and everyone. Check out how they express their mission and pledge to the world in the above founder letter.
What are the current trends/expectations in SentinelOne’s Industry?
Cybersecurity is fundamentally a data problem - Advances in AI, specifically machine learning, where algorithms use data to make decisions with minimal human intervention, are already revolutionizing fields such as healthcare, advertising, and securities trading. AI is ripe for revolutionizing cybersecurity.
Stakes are high for organizations and cybercriminals - The exponential growth of sensitive customer and business data has simultaneously made many organizations the target of highly sophisticated cybercriminals. In addition to the intangible cost of data breaches, for companies that experienced breaches of 1 million to 10 million records, the average cost of a data breach is $50 million, according to IBM Security’s Cost of a Data Breach 2020 report.
Tectonic shifts in IT require a “Zero Trust” operating procedure - With millions of remote laptops accessing thousands of applications running in public, private and hybrid clouds, traditional perimeter-based security controls are bypassed and organizations have to operate in a “Zero Trust” IT environment. Organizations are digitizing and bringing their sensitive data assets online and connecting more devices to their network. As a result, the attack surface has expanded considerably, and the notion of a corporate perimeter protected by firewalls is a relic of the past, making the endpoint the epicenter, and endpoint protection software the first, and last, line of defense. The following tectonic shifts in IT have increasingly left companies vulnerable:
The rapid adoption of cloud computing - Cloud computing has become a strategic imperative for organizations to accelerate their digital transformation. According to IDC, worldwide spending on cloud services is expected to grow at 15.7% annually from 2020 to 2024, to over $1 trillion.
The operating system landscape is more complex than ever before - The diversification of IT and BYOD policies brought Macs and other devices into today’s organizations. IDC’s MarketScape reports that the number of computers that run macOS at U.S.-based companies with 1,000 or more employees increased from 17% in 2019 to 23% in 2021. While Windows remains the dominant operating system for computers, Linux has become widely adopted among organizations to power their business applications and servers.
The proliferation of connected devices - According to IDC, an estimated 41.4 billion IoT devices will be online in 2025. Many of these devices will have little to no built-in security capabilities.
Remote work is here to stay - The COVID-19 pandemic changed the way most organizations operate, accelerating technology’s role in supporting remote work.
Sophisticated cyberattacks circumvent existing security controls -Cyberattacks have evolved from “child’s play” malware into highly sophisticated, organized, and large-scale attacks by malicious insiders, criminal syndicates, and nation-states seeking to circumvent existing security controls and undermine critical societal functions through a variety of attacks that are:
Fast acting - Many attacks, such as Emotet, Maktub, and Medusa Locker, take only seconds for adversaries to breach organizations, exfiltrate data, demand ransoms, and disrupt operations. They bypass security controls that are based on the “1-10-60” rule which evangelizes that organizations have one minute to detect, ten minutes to investigate, and 60 minutes to remediate a security breach.
Stealthy, with long dwell times - Some attacks, such as advanced persistent attacks, or APT, and targeted attacks, are designed to breach the organization and stealthily infiltrate across assets to steal data, facilitate future attacks, or cause other harm over a long period of time, all while operating undetected. The average time to identify and contain a breach is 280 days, according to IBM Security’s Cost of a Data Breach Report 2020, giving threat actors plenty of time to inflict damage. For instance, the recent Sunburst attack that impacted approximately 18,000 organizations across federal, state, and local governments and the private sector, used a variety of sophisticated techniques to disguise its operations as it spread laterally within target organizations over many months.
Cybersecurity teams are unable to scale - While the number of connected devices, applications, and cyber threats has increased exponentially, organizations are facing an acute shortage of skilled cybersecurity talent. (ISC)2 estimates that approximately three million additional professionals are needed today to adequately defend organizations against cyberattacks worldwide. This is further aggravated by the large number of security solutions that companies have deployed over time, many of which generate large volumes of alerts that security teams have to sift through and make sense of. According to the Enterprise Strategy Group (ESG), around 20% of cybersecurity professionals surveyed identify their top incident response challenge as “keeping up with the volume of alerts.”
How do the current Industry Incumbents Lack Innovation and what are their Limitations?
Modern society is digital.
With digital transformation changing everything, accelerated by the COVID-19 pandemic, organizations have become increasingly susceptible to cyberattacks. Every place where data resides is vulnerable from device to server to the cloud. From healthcare to commerce, education to infrastructure, transportation to manufacturing, financial institutions to government agencies, cyberattacks are one of the biggest threats to global stability and progress. Within milliseconds, services we rely on can cease to operate. Our growing reliance on technology creates an accelerating risk cycle: more devices generate and process more data which results in more opportunities for cybercriminals to attack. Cybersecurity is foundational to preserving our digital way of life.
What is a Cyberattack - Any unauthorized attempt to expose, alter, disable, destroy, steal, or gain data.
Cyberattacks have become the output of military-grade, highly resourced, and automated nation-state and cybercrime operations. Cyberattacks are a daily occurrence in every part of the world. Accepted defense mechanisms are failing. Legacy antivirus, powered by human-generated signatures, remains the most widely deployed security technology, despite proving ineffective and reactive. Human-powered EDR emerged as the alternative in which people became the detection and response crew. This approach evangelized the “1-10-60” rule which claimed the best achievable cybersecurity outcome was capped at one minute to detect an attack, ten minutes to investigate, and 60 minutes to respond. Recent ransomware attacks prove it only takes milliseconds to breach an organization, exfiltrate data, and force a complete shutdown. The central problem with legacy antivirus and human-powered EDR is that both rely on linear human effort to defend against the exponential growth of cyber threats. This is akin to bringing a knife to a gunfight.
So what are the limitations of current cybersecurity tools?
They Cover a limited spectrum of cyber threats - Existing tools, such as signature-based approaches, human-powered monitoring, application whitelisting, and sandboxing, are each effective under limited circumstances but lack the ability to detect the full spectrum of threats organizations are dealing with. Signature-based approaches can detect attacks that have been seen previously but are incapable of preventing a wide range of attacks, such as unknown malware, ransomware, modified versions of previously known attacks, and exploits of zero-day vulnerabilities. In addition, they lack the ability to detect and prevent an increasing number of fileless attacks, that deposit no malware, but instead exploit operating system vulnerabilities and use trusted tools within IT environments, such as Office document macros and PowerShell scripts. Application whitelisting relies on manually creating and updating “always allow” or “always block” rules that strain the limited security resources of an organization and are often rendered obsolete, or ineffective in detecting attack vectors embedded in legitimate applications. As a result, despite deploying a myriad of point solutions, organizations have continued to suffer huge losses from cyberattacks.
They Utilize AI approaches that rely on humans to power protection mechanisms - First-generation AI tools cannot handle the volume, variety, and velocity of data that must be ingested and analyzed, in real-time, to be effective in preventing breaches. These tools often rely on ineffective pattern-matching algorithms in the cloud that generate so much “noise” that human intervention is required to extract useful “signals.” Some of those tools transfer the raw data into the public cloud, hoping to leverage the massive compute power available there, but that has not fixed the problem. It has merely shifted the problem elsewhere because AI algorithms are only as intelligent as the quality of the data that they work with as well as the speed at which they operate. Without curated, contextual data, these tools only generate more alerts that need to be analyzed by humans. They cannot take action at machine speed and are thus unable to detect and prevent or stop many fast-acting attacks. Additionally, due to communication latency with the cloud, these tools cannot generate actionable insights in real-time, which is required to stop many current threats. Sunburst and numerous recent breaches have illustrated that these tools are unable to provide the protection that organizations need. Further, because these tools lack the ability to prevent attacks and often do not meet regulatory requirements such as File Integrity Monitoring by themselves, organizations are forced to leave their antiquated antivirus software as “crutches” to satisfy auditors.
Lack of long-term data visibility to proactively investigate advanced threats - Existing EDR tools lack the capability to store large sets of historical data cost-efficiently, and consequently often only offer limited data retention capabilities. This results in only partial datasets being available for threat hunting and time-bound retrospective forensic analysis. Given that the average time to identify and contain a breach is 280 days, limited historical EDR data makes full incident investigation challenging for security personnel, as they are unable to go back in time and see how the attack breached the organization and progressed.
Struggle to protect complex modern IT environments - Existing tools were not designed to protect today’s multi-cloud, multi-device, multi-OS IT environments. Vendors have extended their existing solutions by bolting on functionalities, which has led to a wide disparity of capabilities across endpoints and operating systems. This has resulted in a patchwork of second-class capabilities and a disjointed collection of security tools that significantly increases operational complexity without delivering higher levels of protection. Existing tools further lack the ability to identify unmanaged IoT devices which often have very limited, if any, built-in security capabilities and can be used by attackers to access the networks of target organizations. This lack of unified visibility and control over endpoints, cloud workloads, and IoT devices results in gaps in security coverage for organizations.
Lack of deployment flexibility for organizations - Organizations struggle with the limited deployment methods mandated by existing tools. On-premise tools impose complexity and maintenance burdens on organizations. These tools typically lack the ability to quickly adapt to organizations’ rapidly evolving IT environments, which requires significant upfront investments and configuration and integration efforts. On the other hand, cloud-only cybersecurity vendors are unsuitable for many large and complex enterprises and governments that need private or hybrid cloud solutions to meet their security, regulatory, and compliance requirements.
Inhibit technology workflow automation - Many existing tools lack out-of-the-box APIs and rely heavily on professional services, which makes the integration and implementation process long, expensive, and often unattainable. The lack of flexible workflow integrations limits organizations’ ability to reduce overhead by automating processes, and to improve their security by ensuring that process steps are done quickly, consistently, and according to their predefined requirements.
What does SentinelOne do?
SentinelOne envisioned a revolutionary data and AI paradigm where technology alone could autonomously prevent, detect, and respond to cyberattacks.
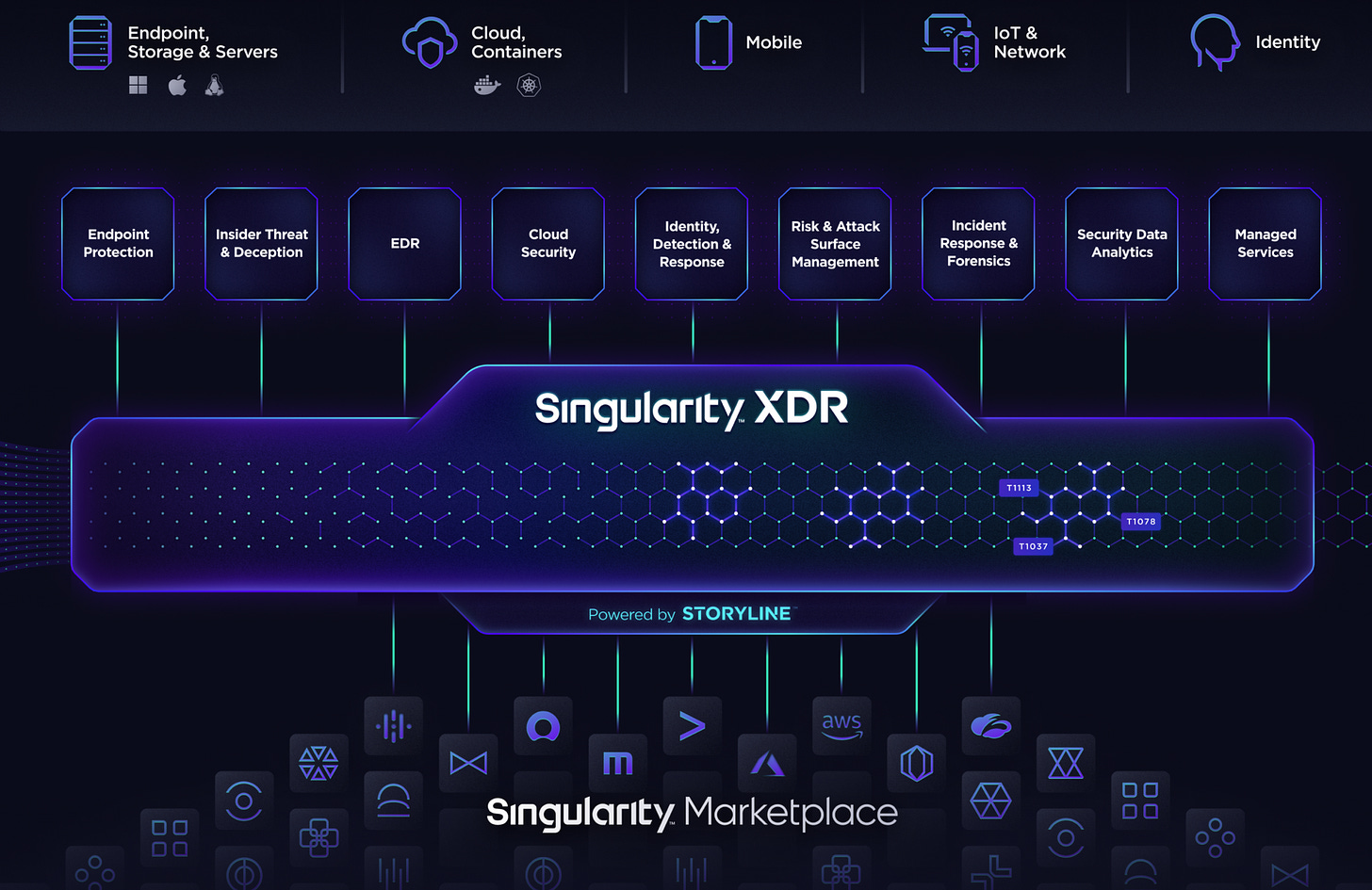
Hence, SentinelOne pioneered the world’s first purpose-built AI-powered XDR platform to make cybersecurity defense truly autonomous, from the endpoint and beyond. SentinelOne's Singularity Platform instantly defends against cyberattacks - performing at a faster speed, greater scale, and higher accuracy than possible from any single human or even a crowd.
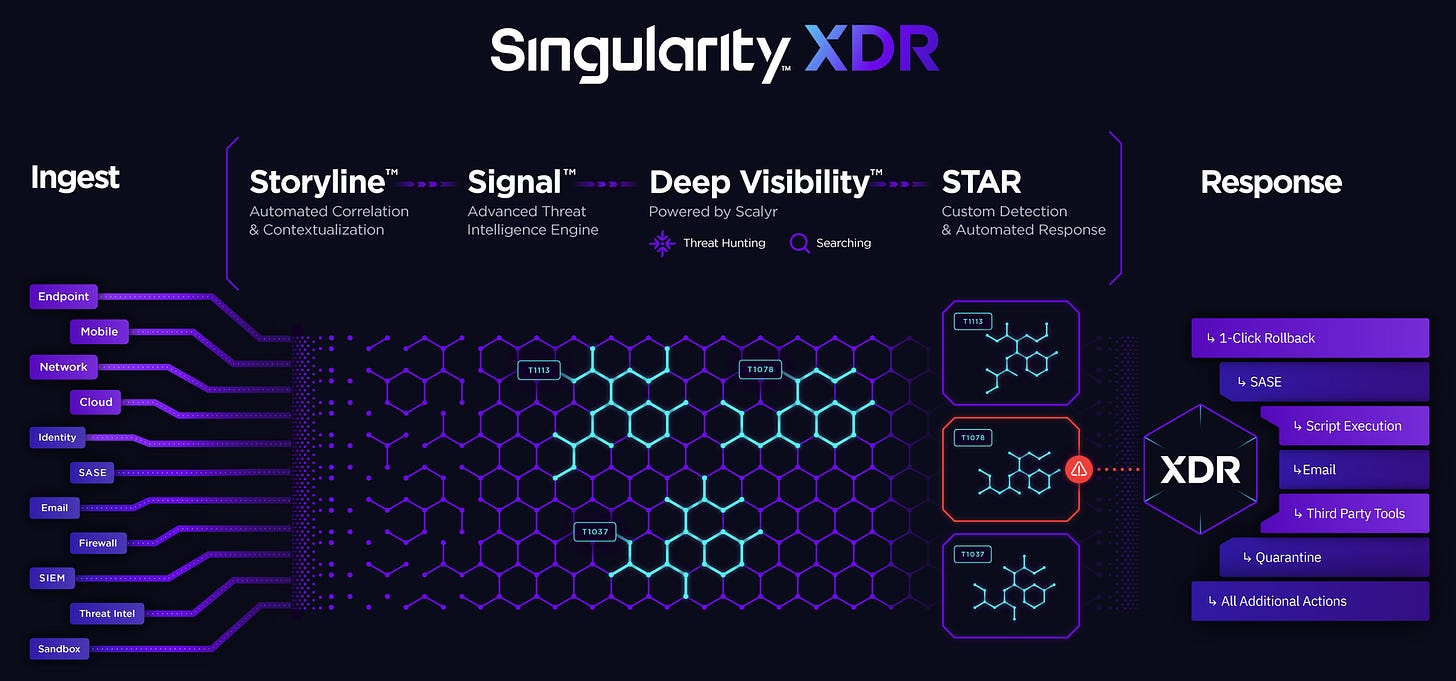
SentinelOne's XDR platform ingests, correlates, and queries petabytes of structured and unstructured data from a myriad of ever-expanding disparate external and internal sources in real-time. They build rich context and deliver greater visibility by constructing a dynamic representation of data across an organization. As a result, their AI models are highly accurate, actionable, and autonomous. Their distributed AI models run both locally on every endpoint and every cloud workload, as well as on their cloud platform. Their Static and vector-agnostic Behavioral AI models, which run on the endpoints themselves, provide customers with protection even when their devices are not connected to the cloud. In the cloud, their Streaming AI detects anomalies that surface when multiple data feeds are correlated. Furthermore, SentinelOne's platform provides visibility across an organization’s digital assets through one console, making it easy and very fast for analysts to search through petabytes of data to investigate incidents and hunt threats. Their Singularity Platform offers multi-tenancy and can be deployed in a diverse range of environments that customers choose, including public, private, or hybrid clouds.
On each endpoint and cloud workload, SentinelOne runs highly optimized AI models in a single lightweight software agent. Their Static AI model predicts file-based attacks of all types, even previously unknown threats, often referred to as “zero-day attacks,” with extreme precision in milliseconds. Their Behavioral AI model maps, monitors, and links all behaviors on the endpoint to create rich, contextual narratives called Storylines. These high-fidelity Storylines are continuously evaluated by SentinelOne's Behavioral AI model. When activity is deemed a threat, their software autonomously takes action to kill the attack. Because Storylines contain a complete record of unauthorized changes made during an attack, they are ready to remediate or roll back these changes. The power to turn back time on a device is unique in the market. It is the ultimate safety net and exemplifies autonomous cybersecurity. Thus, SentinelOne eliminates manual, expensive, and time-consuming incident cleanup.
In the cloud, SentinelOne's platform aggregates Storylines. Their Streaming AI detects anomalies that surface when multiple data feeds are correlated with additional external and internal data. By providing full visibility into the Storyline of every secured device across the organization through one console, their platform makes it very fast for analysts to easily search through petabytes of data to investigate incidents and proactively hunt threats. SentinelOne has extended their control and visibility planes beyond the traditional endpoint to cloud workloads, unmanaged devices, and IoT devices. This empowers security analysts of all skill levels to hunt, investigate, and remediate even the most sophisticated threats across the network leveraging the automated context provided by Storylines. SentinelOne's proprietary data stack and cloud architecture enable them to retain this rich, contextual data on behalf of customers for up to three years(also permanently if that's preferred) in a highly cost-efficient manner.
SentinelOne's Singularity Platform can be flexibly deployed in the environments that customers choose, including public, private, or hybrid clouds. Their feature parity across Windows, macOS, Linux, and Kubernetes offers best-of-breed protection, visibility, and control across today’s heterogeneous IT environments. Together, these capabilities make their platform the logical choice for organizations of all sizes, industry verticals, and compliance requirements. Their platform offers true multi-tenancy, which enables the world’s largest organizations and their managed security providers and incident response partners the best management experience. Their customers realize improved cybersecurity outcomes with fewer people, producing an attractive return on investment.
What are SentinelOne’s Products?
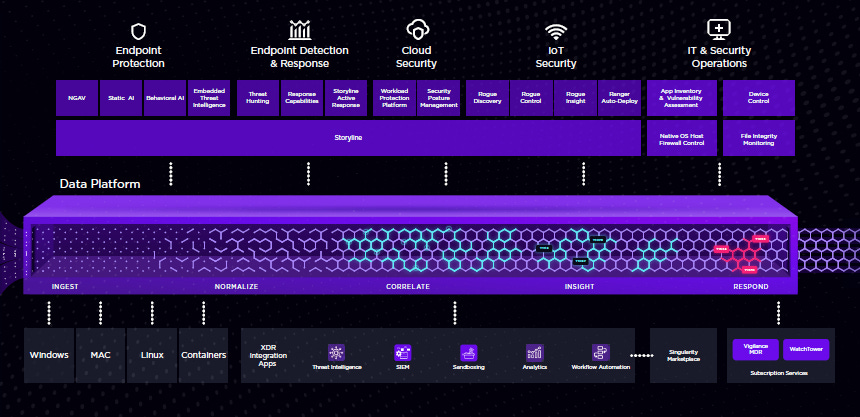
SentinelOne's Singularity Platform delivers AI-powered autonomous threat prevention, detection, and response capabilities across an organization’s endpoints, and cloud workloads, enabling seamless and automatic protection against a full spectrum of cyber threats. SentinelOne built their Singularity Platform to be deployed as a cloud service or in private and hybrid clouds.
SentinelOne's platform capabilities are connected through three key patented technologies:
Data Analytics - SentinelOne's data analytics technology can ingest, correlate, and query petabytes of structured and unstructured data from disparate external and internal sources.
AI - SentinelOne's Static, Behavioral, and Streaming AI technologies run in a distributed manner on our data cloud as well as on every endpoint and every cloud workload they protect.
Storyline - SentinelOne's Storyline technology builds a model of real-time running processes and their behaviors, to create rich, contextual data narratives which become the input to their Behavioral AI model. Storyline powers their unified EPP, EDR, XDR, and platform functionalities. It is the foundation of their EPP while providing unprecedented levels of visibility with contextual information for benign and malicious processes. SentinelOne extends its fundamental protection, visibility, and response capabilities well beyond the endpoint to cloud, and third-party solutions in their Singularity Platform. They designed their platform based on our “design to delight” principle and developed a powerful yet simple and intuitive user experience.
Endpoint Protection
SentinelOne's next-generation antivirus technology provides autonomous real-time protection across all operating systems, including Windows, Linux, macOS, and cloud-native and containerized workloads. Their endpoint protection is powered by distributed AI which resides both on devices as well as in the cloud for always-on, machine-speed protection. It is capable of autonomous decision-making on the device and stopping threats in milliseconds rather than minutes, hours, or even days. SentinelOne is able to provide superior performance compared to traditional signature-based antivirus tools and earlier next-gen antivirus products with the following three key capabilities:
Static AI - SentinelOne's on-device AI model can detect file-based attacks predictively, even those that are previously unknown zero-day exploits, with extreme precision in milliseconds. Their Static AI model is the output of a supervised machine learning cycle that is trained on a continuously evolving data set from billions of files coupled with the data from multiple threat intelligence sources, including their proprietary Embedded Threat Intelligence. SentinelOne achieves industry-leading detection rates by carefully developing and curating training data sets at scale.
Behavioral AI - SentinelOne's on-device AI model continuously scores Storylines from the device to precisely classify individual or group behaviors as benign or malicious. The accuracy of their Behavioral AI is powered by the rich contextual information that is encoded in each Storyline that is being scored. As a result, it is attack vector agnostic because it is not limited to any particular pathway used by attackers to penetrate a system, such as zero day vulnerability exploits and living off the land attacks.
Embedded Threat Intelligence - SentinelOne's cloud threat intelligence system combines threat information from their data analytics and research teams, Vigilance MDR and IR services, and other commercial and proprietary threat feeds.
Endpoint Detection and Response
Unlike first-generation EDR products that are reactive and mainly focused on collecting data, SentinelOne's ActiveEDR solutions leverage Storylines to reduce analysis time and to automate response actions by:
Significantly minimizing the time between detection and response through technology automation;
Enabling on-device behavioral analysis, auto-remediation, and response in a fully autonomous fashion; and
Reducing analysis time and requirements for specialized skills by providing technology-generated context which would otherwise need to be produced by highly skilled people manually in a time-intensive and error-prone fashion.
SentinelOne's approach “democratizes EDR,” bringing what was once only usable by seasoned analysts to IT professionals of all levels of expertise. SentinelOne does this without compromising on any EDR functionality sought by power users and advanced security operation centers, or SOCs. From retrospective hunts to remote shells, ActiveEDR excels at visualizing context, pinpointing anomalies, and providing a variety of granular responses.
The main capabilities of ActiveEDR are:
Deep Visibility Threat Hunting - Deep Visibility Threat Hunting provides an easy-to-use search interface on top of its Deep Visibility dataset. This helps security analysts as they hunt for Indicators of Compromise, or IoCs. The search interface is powered by their S1QL language, a user-friendly and intuitive search language streamlined for threat hunting use cases. Features like query auto-completion, drill-downs that facilitate filtering and sorting, and interactive annotated process tree visualization make it easy for entry level analysts as well as highly skilled analysts to be more proficient with S1QL. As a result, analysts can analyze results faster, review more alerts, and be more productive with the power of technology. The Storylines shown within Deep Visibility hunts enable one-click responses, which are far easier and faster to execute than manually scripting responses.
Response Capabilities - SentinelOne's Singularity Platform offers one of the broadest sets of response actions in the EDR market today. Leveraging Storylines, they automate responses or make them optionally initiated by operators. Their response capabilities include:
Kill - Surgically stops the execution of a single process or a whole process group, instantly.
Quarantine - Moves and encrypts threat artifacts from the location in which it was found into a special quarantine directory.
Remediation - Deletes all files and system changes created by the threat.
Remote Shell - Provides full shell capabilities, PowerShell on Windows and Bash on macOS and Linux, directly and securely from the Singularity XDR console. Remote Shell represents a powerful method of responding remotely to events and obtaining additional forensic information.
Rollback - Uses Storylines as a manifest to restore files and system changes impacted by a threat from secured VSS snapshots. Rollback undoes changes with a single-button click or automatically, precisely and deterministically reversing threats and restoring devices to a healthy and secure state.
Storyline Active Response - SentinelOne's Storyline Active Response, or STAR, gives users the capability to set custom IOC-based rules for real-time analysis, alerting, and automatic response workflows. SentinelOne's STAR module is also capable of ingesting threat intelligence feeds to enhance and correlate analyses. The STAR module uses Streaming AI technology to match billions of events to tens of millions of IOCs at the time of ingestion. STAR is a threat hunting and workflow orchestration force multiplier. Without STAR, it is difficult for security analysts to keep pace with the number and complexity of emerging threats from an EDR perspective.
Data Retention - Modern attacks can take days and weeks to initiate after infiltration. Therefore, it is critical for an EDR solution to provide visibility for extended periods of time. This enhances both retrospective analysis and proactive hunting measures. SentinelOne's platform has been designed and built to support extended data retention to time periods that far exceed what others are able to offer, and do so on a cost-efficient basis due to their data retention architecture. SentinelOne offers data retention for up to three years to provide maximum value from their Deep Visibility Threat Hunting module.
Leveraging their data retention capabilities, SentinelOne constructed Binary Vault to store a copy of every known binary, both benign and malicious, that executes across an enterprise. This enables an optional capability for advanced security analysts to download a copy of any file that has been executed in their environment for forensic review and reverse engineering and provides them with access to a broader dataset and more complete lookback capabilities than any of SentinelOne's competitors. In addition, this large repository of benign and malicious binaries enables SentinelOne to continuously improve its AI models.
Remote Script Orchestration - In incident response situations, rapid artifact extraction and endpoint state querying across the entire enterprise is critical. SentinelOne's remote script orchestration module allows concurrent execution of custom and preset scripts across an enterprise, instead of having to triage with a device-by-device approach. By converging their protection, detection, and response capabilities with remote script orchestration, SentinelOne's platform is the only solution that is needed to respond to a breach.
Cloud Workload Security
As more organizations migrate their workloads to the cloud and re-platform on cloud services, adversaries follow the data. Because these workloads are hosted on public cloud infrastructure, they are even more vulnerable. When organizations move to public cloud infrastructure, a typical assumption is that the cloud service provider takes care of all configuration and security. This is not the case and a lot of responsibility is carried by the organization to secure OS, middleware, runtime, data, and applications. Coupled with the standardization of public cloud services with highly accessible APIs and open documentation, this shift leaves a well-marked open door for nefarious actors. SentinelOne's cloud security offerings have been purpose-built for these novel attack surfaces. SentinelOne offers their AI-powered Cloud Workload Protection or CWPP, and Cloud Security Posture Management, or CSPM, to address these threats in the public cloud.
Cloud Workload Protection Platform
EPP and EDR - SentinelOne offers full-fledged EPP and EDR for servers, virtual machines, and containerized workloads. Their runtime protection delivers prevention, detection, response, and hunting functionalities purpose-built for these environments. These capabilities are offered within their single console, streamlining management and meeting anti-malware, regulatory, and compliance needs for server and cloud computing. SentinelOne's efficient one agent per node architecture supports self-managed Kubernetes and managed Kubernetes services, including AWS EKS, Azure AKS, and Google Cloud GKE.
Cloud Application Control - SentinelOne's Cloud Application Control locks down the running image of servers and containers to prevent configuration drift and protect against unauthorized changes, in line with best practices for cloud workload security. SentinelOne is one of the few vendors to offer cloud application control. This capability enables cybersecurity and IT teams to continuously regulate changes within their cloud environment, increasing the overall reliability and security of their services.
Cloud Security Posture Management
Cloud Configuration Management Database - For servers running in the cloud, SentinelOne's CWPP Cloud Workload Security module syncs cloud asset information with their Singularity Platform. This cloud asset information captures the meta-data of the cloud providers like host, network, application information, and tags, which can be used to dynamically group the servers, and apply policies, and is used in their reporting module for operational and configuration insights. As cloud environments rapidly expand and contract in terms of server and compute resources, SentinelOne's CCMDB enables proactive management and provides an accurate and real-time operational picture without having to reconcile data from multiple sources.
Configuration Audit and Risk Scoring - Organizations migrating to public cloud infrastructure need to secure their workloads by enforcing hardening guidelines for cloud-native services. AWS, Azure, and Google Cloud provide hundreds of services, many of which come with their own unique security models. There is far more complexity in public cloud security management than organizations had to contend with in their own private data centers. SentinelOne's planned Configuration Audit Risk Scoring, or CARS, module helps organizations secure their cloud services by automating the controls necessary to secure their cloud footprint.
IoT Security
SentinelOne's IoT Security modules, also known as Ranger, leverage the presence of SentinelOne's software in an organization’s network to track assets, create an Enterprise Asset Map, perform network segmentation, deploy their agents to unprotected devices, and provide risk scores. Ranger transforms SentinelOne's agents into an AI-powered intelligent scanning mesh. Using passive and active techniques, Ranger discovers connected devices, including virtual machines, containers, and IoT devices such as printers, smart TVs, and thermostats. SentinelOne's approach delivers network inventory and risk mapping with no additional software or hardware deployment. Ranger has four key component features:
Rogue Discovery - Enables administrators to identify unprotected or “rogue assets” and verifies SentinelOne's agent is installed on all corporate assets. From a compliance perspective, this feature is useful in ensuring security coverage across large and distributed organizations as well as when integrating newly acquired companies or business units.
Ranger Insight - Provides in-depth information about each discovered device, including open ports, header and application versions, and vulnerability information. Insight augments traditional vulnerability management programs by providing a clear picture of the inventory and risk in the IoT environment.
Rogue Control - Creates network segments to restrict access to a corporate network. Much like the features of a network access control, or NAC, solution, Rogue Control prevents unsanctioned devices, such as guest machines, from connecting to authorized networks. Organizations benefit by eliminating the risk of attackers gaining access to and moving laterally within the network.
Ranger Auto-Deploy - Rapidly deploys SentinelOne's agents using service credentials to unprotected endpoints with no additional IT infrastructure or software. Auto-Deploy provides security teams with complete, instant asset coverage without having to rely on their IT teams’ schedules and priorities to deploy security software.
IT and Security Operations
SentinelOne's Singularity Platform enables security and IT teams to identify vulnerabilities, fix insecure configurations, and manage endpoints. Vulnerable and mis-configured applications make it easier for attackers to gain entry and evade detection. Addressing these vulnerabilities and mis-configured settings strengthens the security risk profile of customers. SentinelOne's platform has the following capabilities:
Application Inventory - Maintains a software application inventory across an entire organization, by capturing the list of installed applications and their attributes such as their version numbers, install date, and publisher.
Scanless Vulnerability Assessment - Using SentinelOne's real-time organization-wide Application Inventory database, SentinelOne's solution is able to provide highly accurate and dynamic Vulnerability Management information without the need to deploy another solution.
Device Control - Allows maximum granularity and flexibility when defining Device Control policies to prevent data exfiltration and malware entry. SentinelOne's Device Control module supports two main media types: USB and Bluetooth devices.
Native OS Host Firewall Control - Leverages native operating system infrastructure to provide an application-aware and location-aware endpoint firewall orchestrator for remote devices.
File Integrity Monitoring - File Integrity Monitoring, or FIM, gained popularity in the early 2000s as the PCI DSS required the implementation of FIM products to track unauthorized changes to critical system files. The data collected by SentinelOne's Deep Visibility EDR can be used to replace traditional file integrity monitoring solutions.
WatchTower
WatchTower is a subscription software offering that provides intelligence-driven, cross-platform threat hunting to help customers adapt to the modern threat landscape through visibility and actionability to novel attacker techniques, global APT, campaigns, and emerging cybercrimes. As SentinelOne tracks threat actors globally, WatchTower parses, consolidates, and contextualizes threat intelligence sources and hunts for threats in our customers’ environments. WatchTower distills intelligence down to its most valuable insights, such as a summary bulletin of the threat, its impact on customers’ organizations, and how the threat can be addressed.
Vigilance MDR
Vigilance MDR leverages the expertise of SentinelOne's in-house security analysts to review, act upon, and document every threat that SentinelOne's Singularity Platform autonomously identifies. It adds a human lens to cybersecurity understanding and augments customers’ in-house security teams. Due to the autonomous nature of our Singularity Platform, Vigilance MDR provides rapid response times to threats. SentinelOne's optional, technology-powered digital forensics analysis and incident response, offering takes Vigilance MDR two steps further and provides customers with a full-service solution.
How does SentinelOne make money?
SentinelOne generates revenue from subscriptions to the Singularity Platform. Customers can extend the functionality of their subscription to the platform by subscribing to additional Singularity Modules. Subscriptions provide access to hosted software. They recognize revenue for performance obligations ratably over the contractual term. Premium support and maintenance and other Singularity Modules are distinct from subscriptions and are recognized ratably over the term as the performance obligations are satisfied.
They invoice customers upfront upon signing for the entire term of the contract, periodically, or in arrears. Most of their subscription contracts have a term of one to three years.
SentinelOne's Singularity Platform Tiers and Modules
SentinelOne's Singularity Platform is primarily hosted in AWS in multiple regions - North America, European Union, Asia Pacific, and AWS GovCloud. They also support deploying their platform in the Google Cloud Platform as well as customers’ on-premise data centers, and private, and hybrid cloud environments for organizations with specialized hosting and data sovereignty needs.
SentinelOne's platform provides feature parity across Windows, macOS, and Linux. It provides customers with full flexibility through a multi-tier offering priced on a per agent basis, which generally corresponds with an endpoint, server, virtual machine, or host. The tiers of SentinelOne's Singularity Platform include:
Singularity Core - SentinelOne's entry-level security solution for organizations that want to replace antivirus tools with SentinelOne's EPP. Singularity Core includes SentinelOne's Static and Behavioral AI models and autonomous threat response and rollback features.
Singularity Control - Made for organizations seeking best-of-breed security with the addition of SentinelOne's “security suite” features for endpoint management. It provides additional features for controlling network connectivity, USB and Bluetooth peripherals, and uncovering rogue devices.
Singularity Complete - SentinelOne's flagship offering includes their full suite of product capabilities.
What is SentinelOne’s customer value proposition?
Protects against present and future cyber threats - A combination of SentinelOne’s powerful Static AI and Behavioral AI on the device with Streaming AI models in the cloud addresses the full spectrum of attacks in an evolving threat landscape, including ransomware, known and unknown malware, trojans, hacking tools, memory exploits, script misuse, bad macros and “living off the land,” or file-less, attacks.
Enables protection and visibility across all digital assets - SentinelOne’s Singularity Platform provides organizations with their full suite of real-time threat prevention, detection, and remediation capabilities across all of their endpoints, cloud workloads, servers, and operating systems. Their platform further leverages their agents, combined with passive and active network discovery methods, to provide customers with organization-wide visibility into all of their network assets, managed and unmanaged. This allows customers to identify potentially vulnerable endpoints and either add protection or isolate them from the network.
Provides autonomous protection and remediation - Powered by SentinelOne’s AI and Storyline technology, their agents defend and heal endpoints autonomously and in real-time by stopping malicious processes, quarantining, remediating, and even rolling back events to surgically keep endpoints clean. Rollbacks are performed autonomously and in real-time, eliminating the need for manual, expensive, and time-consuming incident cleanup.
Enables facilitated, as well as fully-automated, incident investigation and proactive threat hunting - SentinelOne’s platform gives security teams the ability to search their IT assets for behavioral indicators via a single-click interface. Their deep visibility and contextual data empower security analysts of all skill levels to run queries at very fast speeds and quickly understand the root causes behind the most complex threats. Their watchlists further lighten the load on security teams by giving them the ability to schedule customized and fully automated threat hunting searches according to their own criteria.
Provides full forensic recall for complete remediation - SentinelOne offers customers the ability to retain rich, contextual data for up to three years in a highly cost-efficient manner. This forensic data helps customers to investigate breaches that have stealthily infiltrated their organization and operated undetected for many months. It gives them the ability to ensure that any incident has been fully remediated without the need to reimage or replace elements of their IT infrastructure.
Provides a superior customer experience - SentinelOne puts the user at the center of its product development and engineering processes. The combination of their intuitive and clean user interface, their ability to provide context with one click, and their high degree of automation empowers customers to use their platform independent of their expertise level. As a result, their customers report a 97% Customer Satisfaction Score and an NPS of 70.
Delivers rapid time to value - By deploying SentinelOne’s Singularity Platform, customers can receive a return on investment of 353% over three years, and a payback period of fewer than three months according to a 2020 Total Economic Impact study that SentinelOne commissioned and that was conducted by Forrester Consulting. SentinelOne’s Singularity Platform can be quickly and easily deployed in the diverse IT environments of customers and without extensive configuration or maintenance.
Who are SentinelOne’s Customers?
Some of their notable customers are:
Estée Lauder, Aston Martin, JetBlue, Norwegian Airlines, Red Robin, TGI Fridays, Wynn, Blizzard, Electronic Arts, Pandora, Autodesk, Fiverr, Nutanix, NVidia, Wells Fargo
What are some successful Customer Case Studies?
Aston Martin Lagonda
Situation: Aston Martin Lagonda is the world’s only independent luxury car group with more than 100 years of design and automotive excellence. The group strives to be the most agile and efficient company in the luxury segment. Facing an evolving threat landscape, Aston Martin began its search in 2018 for a cloud-native endpoint security platform that would better secure against modern malware and ransomware attacks than its incumbent legacy anti-virus tool. Aston Martin’s complex IT environment required the new solution to deliver world-class protection at scale without any disruptions.
Solution: After Aston Martin shortlisted three major EPP & EDR platforms, it was clear to the team that SentinelOne offered automation, artificial intelligence, and machine learning capabilities that no other vendor in the endpoint security market could match. In a proof-of-concept, SentinelOne outperformed the rest of the pack, maximizing protection while minimizing operational overhead. The team also recognized the peace of mind they could gain by enlisting SentinelOne’s Vigilance MDR analysts for 24/7/365 scalability and protection. What followed was the rapid deployment of Singularity Complete and Vigilance. In 2019, SentinelOne was designated as Aston Martin Lagonda’s Official Cybersecurity Partner—a partnership that continues today as SentinelOne delivers state-of-the-art technology for Aston Martin’s constantly-innovating team as well as the Aston Martin Cognizant Formula One team.
“In selecting our Official Cybersecurity Partner, SentinelOne was playing against some very well-established players in the field—and it was a lot more compelling than what the rest were bringing to the table. Our partnership today is stronger than ever, and we can innovate and grow with confidence knowing we’re backed by world-class, future-proof technology.”- Information Technology Director, Aston Martin Lagonda
Xylem Inc.
Situation: Xylem is a leading water technology company committed to “solving water” by creating innovative and smart technology solutions to meet the world’s water, wastewater, and energy needs. Xylem delivers innovative water technology solutions throughout the cycle of water. For this reason, Xylem’s team searched for a dependable, scalable, and cutting-edge endpoint security solution in 2019 to keep its systems up and running with confidence. Given the unique attack surface Xylem’s IT and Security teams are tasked with protecting, they needed a partner who could comprehensively secure all major operating systems and support the full range of devices comprising Xylem’s digital environment.
Solution: Following a thorough evaluation of next-gen EDR solutions available, we emerged as the clear choice for Xylem because of our robust feature set, ease of implementation and use, and support for all major operating systems. In addition to Singularity Complete for EPP and EDR, Xylem also desired a solution which would enhance visibility and provide control of internet-enabled devices on the network, and saw significant value in our Singularity Platform’s Ranger offering. We continue to deliver business value for Xylem, as protection against known and unknown attacks without human interaction and efficient, effective investigative, and forensic capabilities for Xylem’s analysts has significantly reduced the effort and time needed to fully address threats. Two years later, Xylem continues to trust us as its endpoint security partner not only for protection against today’s evolving threats, but also for expertise and guidance through our Technical Account Management and Vigilance MDR services.
“Quite simply, SentinelOne provides us greater confidence. Since development, we’ve experienced a significant decrease in the need to reactively respond to threats which might impede and impact our business, enabling Xylem to focus on serving our customers and communities around the world.” - Chief Information Security Officer, Xylem Inc.
What do SentinelOne’s current Financials look like?
Now, let's dive into some brief financials.
Revenue - $339M 2022Q1
ARR Growth - 110% 2022Q1
Gross Margin - 65% 2022Q1
Earnings Margin - negative 115% 2022Q1
Net Cash - $1.6BM, kinda crazy, incredibly well capitalized
EV - $6.3B
EV/Revenues - 18x
Dollar Based Net Retention Ratio - 131%
Customers - 7450 overall, 591 customers with more than $100K ARR
TAM - $40B
Their current guidance implies ARR going over $400M.
Now looking at the losses, you might think this is a bad investment. Watch out for significant gross margin expansion, operating leverage, cash pile, high retention, stickiness of their products, and hypergrowth that will power SentinelOne to generate substantial returns over 5+ years.
Now Let's look at what sort of a return we can expect from SentinelOne over the next 5 Years
Keep reading with a 7-day free trial
Subscribe to Modern Growth Investing to keep reading this post and get 7 days of free access to the full post archives.